
FaceTime Like a Pro
Get our exclusive Ultimate FaceTime Guide 📚 — absolutely FREE when you sign up for our newsletter below.

FaceTime Like a Pro
Get our exclusive Ultimate FaceTime Guide 📚 — absolutely FREE when you sign up for our newsletter below.
Protect your iPhone and data with these 10 quick security tips.
These days, our iPhones do a lot more than make calls or send texts—they carry our daily lives. They hold a treasure trove of personal information, from managing money and checking emails to tracking health and staying connected on social media. That kind of access makes them a tempting target for hackers and scammers.
As awareness grows around remote work scams, ghost jobs, and data exploitation in the job market, protecting your data is more crucial than ever. This guide breaks down the essentials of iPhone security, especially for younger, diverse professionals navigating digital life and career development.
Cyber threats refer to malicious activities that target your personal or organizational information through digital means. These include hacking, phishing, spyware, and ransomware attacks. iPhones, while often perceived as secure, are not immune. Cybercriminals are constantly evolving their methods, which harvest personal details to social engineering schemes designed to bypass even the most secure apps.
Whether you’re applying for jobs, swiping on dating apps, or checking your bank balance, the threat is real: data breaches can lead to identity theft, financial loss, and even long-term career damage.
If you’re serious about staying ahead of cybercriminals, here are ten smart, actionable steps to safeguard your iPhone:
Two-factor authentication adds an extra layer of protection by requiring a second form of verification (usually a code sent to another device or app). Even if someone gets your password, they won’t be able to access your accounts without that second step.
Tip: Set up 2FA for Apple ID, iCloud, email, and any app that offers it.
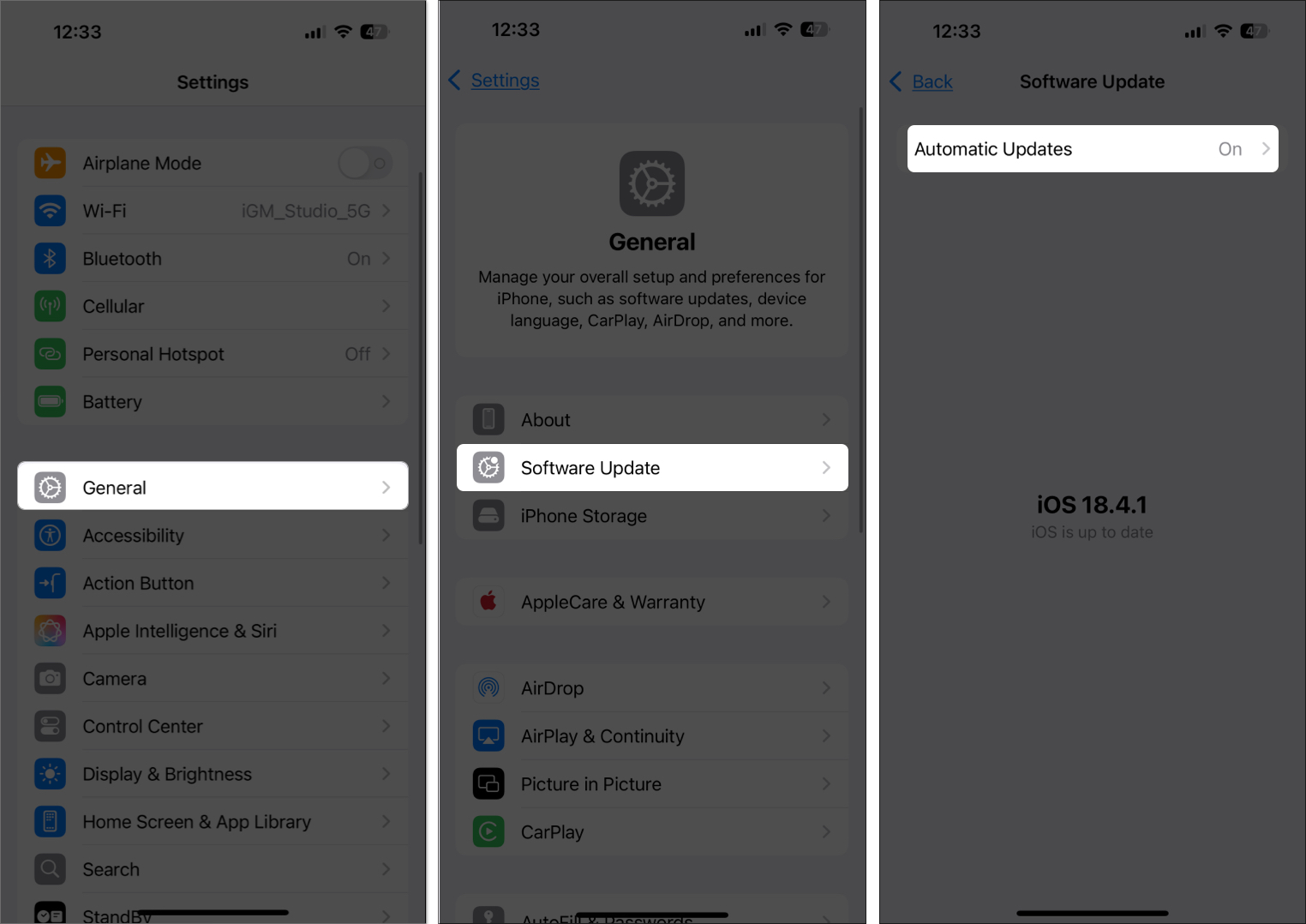
Apple frequently releases updates that fix bugs and security vulnerabilities. Delaying these updates can leave you open to known exploits.
Tip: Turn on automatic updates under Settings > General > Software Update so your iPhone stays protected.
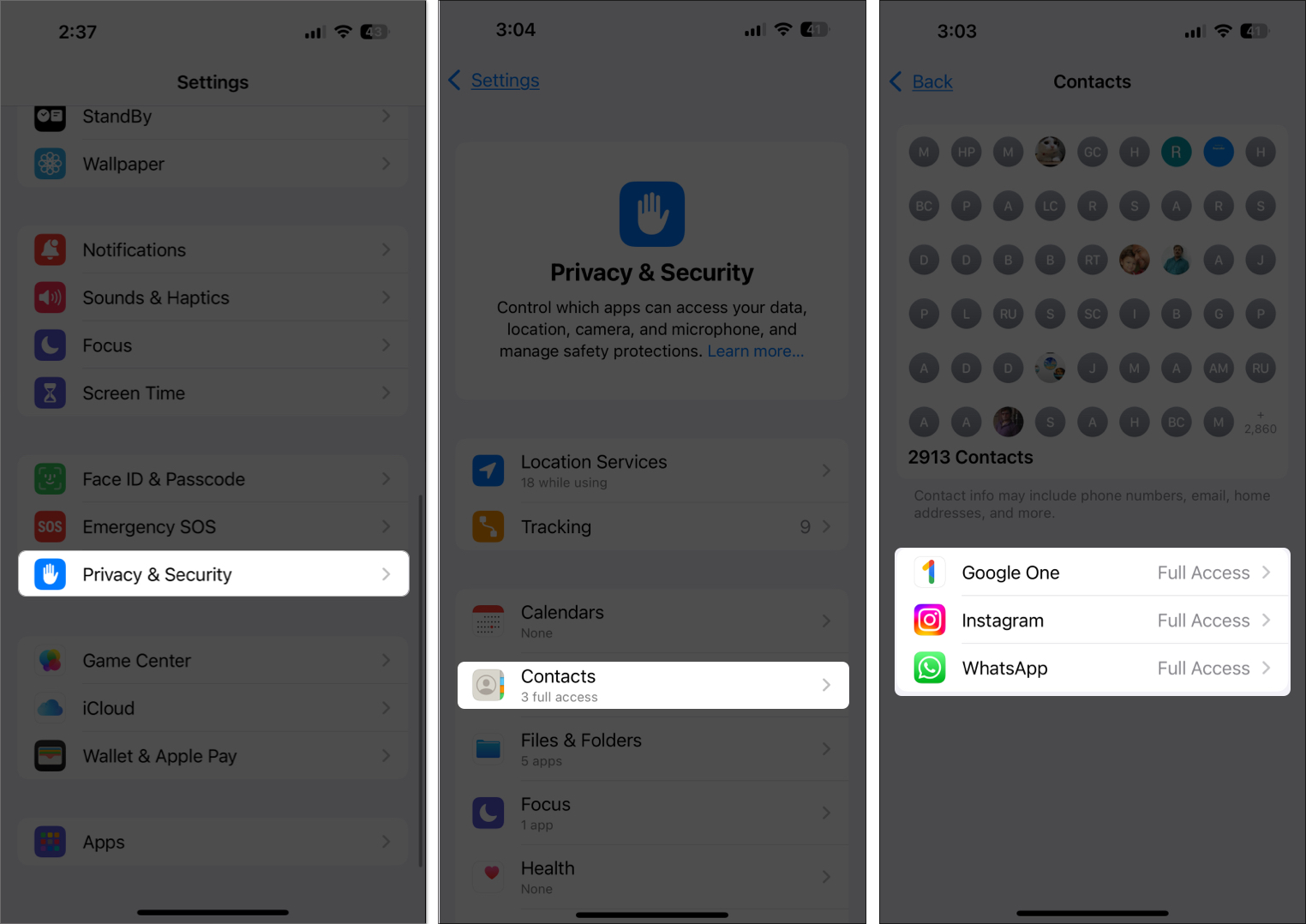
Many apps ask for permissions they don’t need, such as access to your camera, microphone, or contacts.
Tip: Go to Settings > Privacy & Security and review app permissions. Revoke access to anything unnecessary.
Using the same password for multiple accounts is a recipe for disaster. One breach can snowball into several compromised accounts.
Tip: Use Apple’s built-in password app or a reputable third-party app to generate and store strong passwords.
Using public Wi-Fi is a common part of modern life, especially for students and remote workers. But it’s also a hotspot for cyber threats. A VPN encrypts your internet connection, keeping your activity and data private.
Tip: Download a VPN before logging into any public Wi-Fi networks like those in coffee shops or co-working spaces.
Biometric security makes it harder for someone to access your phone without your permission. It’s quick, convenient, and more secure than a passcode alone.
Tip: You can also require Face ID for specific apps like banking or password managers for added protection.
Leaving Bluetooth or AirDrop on all the time makes it easier for nearby attackers to connect to your device.
Tip: Swipe down to access Control Center and toggle off these features when not in use.
Phishing isn’t just a desktop problem. Malicious links in text messages, emails, or even social media DMs can compromise your data instantly.
Tip: If it looks sketchy, don’t click it. And don’t download attachments unless you’re 100% sure they’re safe.
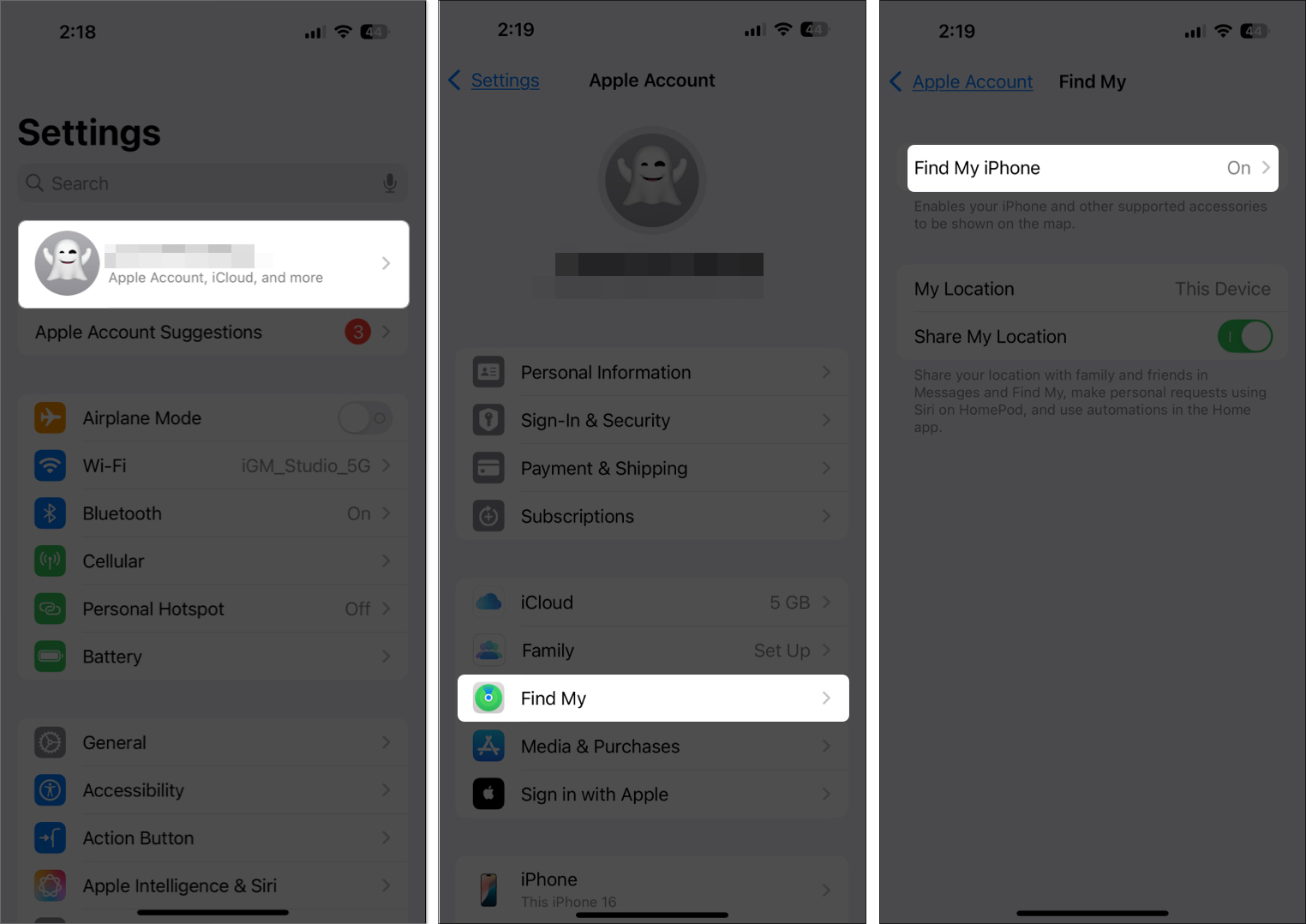
If your iPhone is lost or stolen, Find My iPhone allows you to locate, lock, or erase it remotely.
Tip: Go to Settings > Your Name > Find My > Find My iPhone to activate it and make sure Send Last Location is enabled.
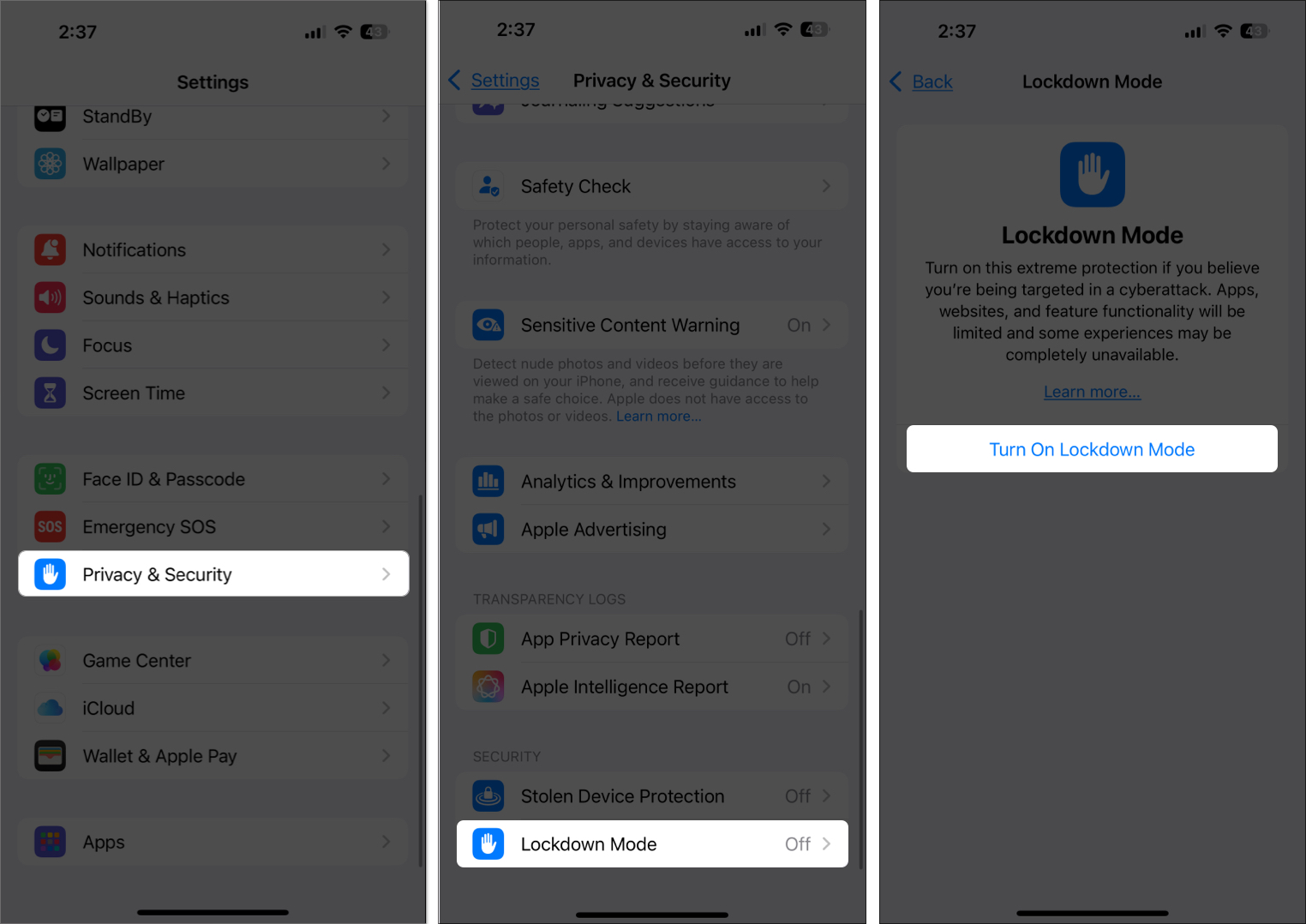
Introduced in iOS 16, Lockdown Mode is designed for users who may be personally targeted by sophisticated threats (journalists, activists, etc.). But anyone can enable it for maximum protection.
Tip: Go to Settings > Privacy & Security > Lockdown Mode. It disables many potentially vulnerable features and blocks unknown communication attempts.
I’ve learned the hard way just how much of our lives are tied to our phones – banking apps, personal photos, work emails, and even job applications. It’s all there, and honestly, I didn’t think much about security until a sketchy link almost cost me access to everything. That experience was a wake-up call.
If you’re applying for jobs, building your profile online, or just trying to keep your private life private, don’t wait for something to go wrong. Take your iPhone security seriously now.
Start with the basics: update your device, use strong passwords, and be careful about what you download or click. Building good habits doesn’t take long, and it’s worth it for the peace of mind.
Trust me – protecting your data is one of the smartest things you can do. And if someone you know could use this advice, send it their way. It’s always better to be safe than sorry.