In this age where we use our phones for all sorts of online transactions and payments, nothing can be quite disconcerting than learning that the passwords to your online accounts have been compromised.
Fortunately, iPhones have a built-in password monitoring system that allows you to see compromised passwords on your iPhone, make an audit of your account information, and detect data leaks. Rushing to check for compromised passwords on your iPhone? I’ve got you!
- What is Apple’s “Security Recommendations” feature?
- What is a data leak?
- How to view compromised passwords on iPhone
- How to hide a security recommendation
- Disable my iPhone from detecting compromised passwords
- How to protect yourself against data leaks
What is Apple’s “Security Recommendations” feature?
Apple’s Security Recommendations is a password monitoring feature embedded in their iCloud Keychain service. Introduced in iOS 14, this cybersecurity feature continually checks the passwords saved in your Password Autofill keychain and sees whether they’re found in recognized databases of leaked passwords.
Security Recommendations are divided into two sections: High Priority Recommendations include accounts that use a compromised password, while Other Recommendations typically list accounts where you reused a password or if the password is weak and easy to guess.
What is a data leak?
A data leak is an incident where private or confidential information like passwords is accidentally or intentionally released in an untrusted environment. It is usually a result of weak security controls and vulnerabilities in systems, networks, or apps.
So what does it mean when your password has appeared in a data leak? It means that your password has been compromised, and your account is no longer secure.
How to view compromised passwords on iPhone
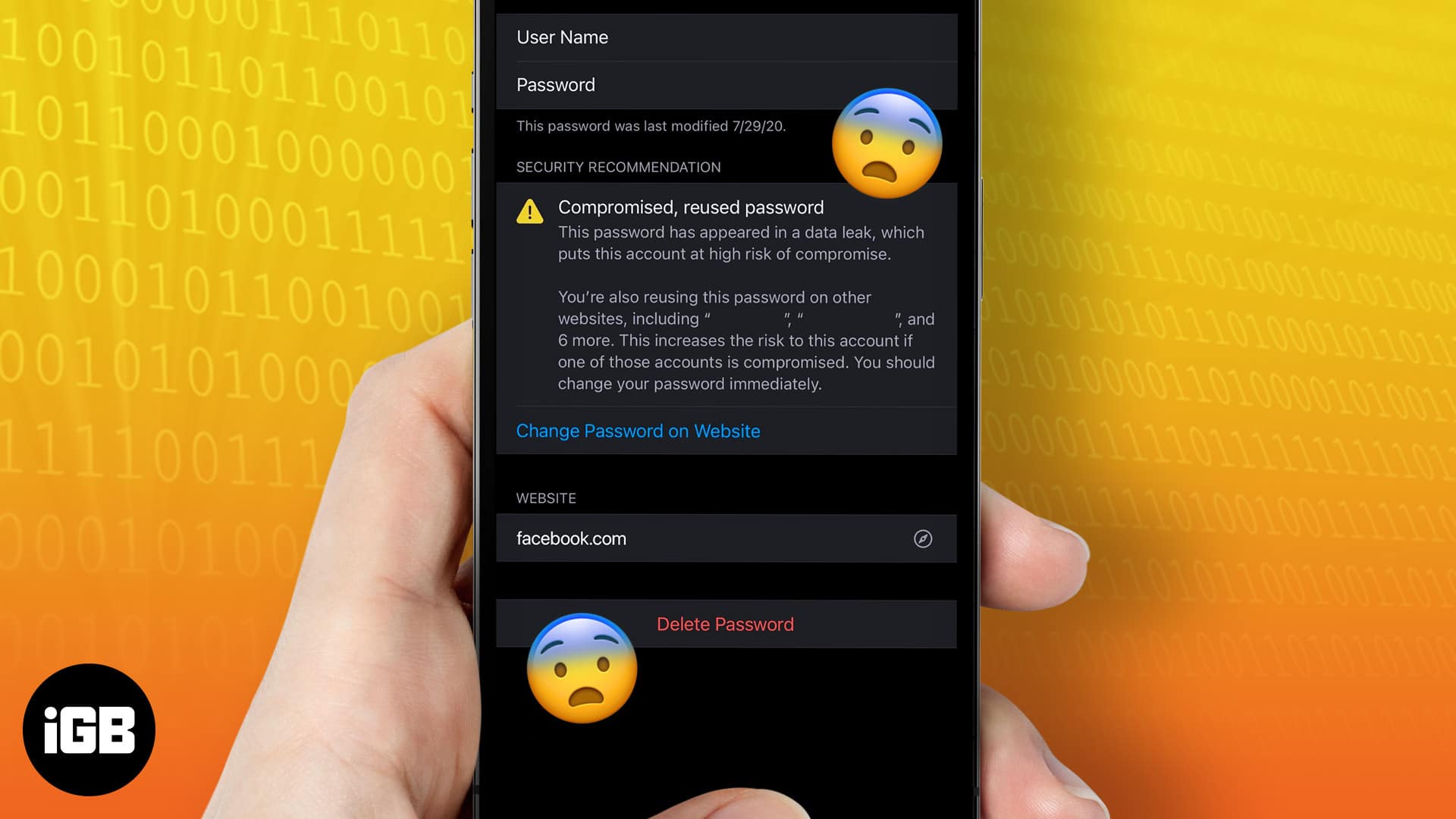
As soon as your passwords match a password found in a data leak, your iPhone will immediately send you an alert with the heading “Compromised Passwords.” However, your iPhone may not do this until you attempt to log in to an affected account.
You don’t have to wait for an alert, though. You can always access the list of compromised passwords in Settings. This is also where you can find your saved passwords on your iPhone
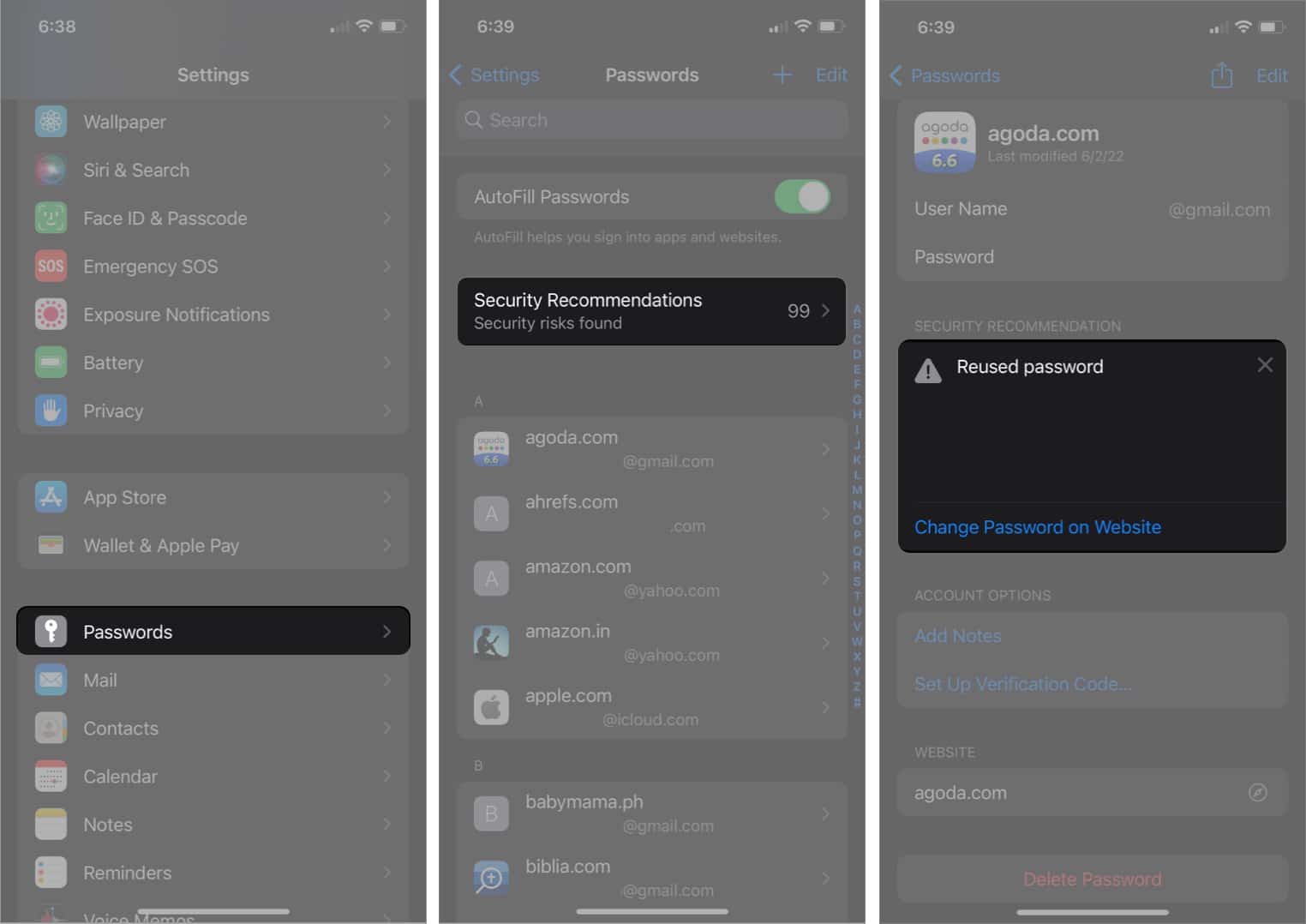
- Go to Settings → Passwords.
- Enter your passcode, Face ID, or Touch ID.
- Tap Security Recommendations if visible to find reused or compromised passwords.
- Select an account → tap Change Password on Website.
You’ll be redirected to the site or app to manually change your password.
How to hide a security recommendation
Hiding a security recommendation may be helpful when you’re reviewing the list. Besides, there are account concerns that you can’t or don’t want to address:
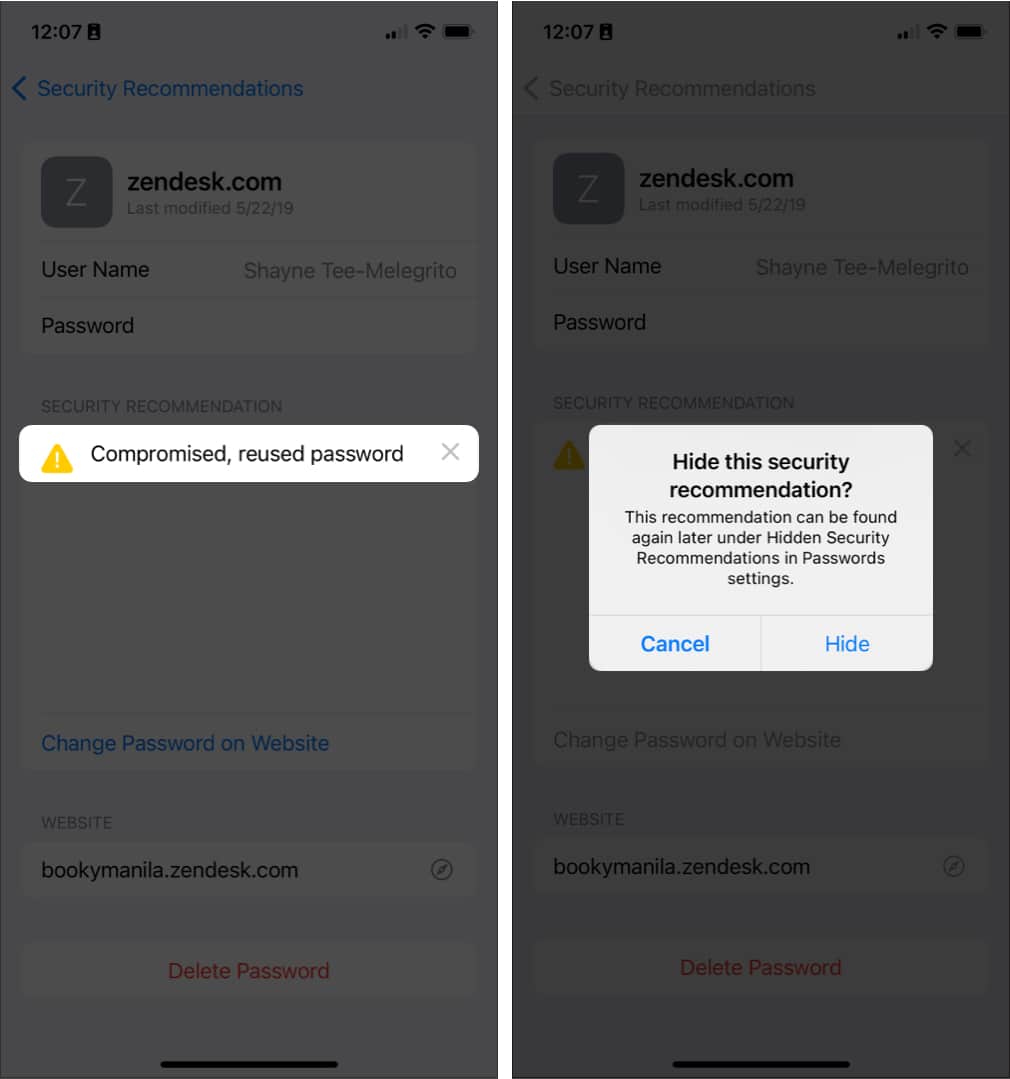
- Go to Settings → Passwords → Security Recommendations.
- Select an account → tap the x button on the Security Recommendation section → choose Hide.
You can still view the recommendations you’ve hidden: go back to Security Recommendations → scroll to the bottom and tap Hidden Security Recommendations → select Reset Hidden Security Recommendations. This will reshow all the hidden security recommendations.
Disable my iPhone from detecting compromised passwords
If you find the feature irrelevant and do not want your iPhone to alert if your passwords appear in known data leaks, there is an option to turn it off.
Go to Settings → Passwords → Security Recommendations → toggle off Detect Compromised Passwords.
How to protect yourself against data leaks
While you don’t have complete control of data leaks, there are measures you can take to protect your accounts against them.
1. Update your software
Software and networks regularly suffer from security vulnerabilities that hackers can exploit to attack them. Developers release regular security updates.
While updating your iPhone apps can be inconvenient, it’s way better than allowing hackers to access your personal information and potentially ransack your accounts.
2. Regularly change your password
Many apps, especially banking and online payment systems like PayPal, regularly ask you to change your password for a reason. Doing so keeps your accounts secure and ensures that hackers only stay inside your account for a short time if your account gets compromised.
However, this may not be necessary if you have a strong password. iPhones and iPads also allow you to quickly generate and save strong passwords.
3. Be careful using password managers
Password managers are generally secure. They use a zero-knowledge architecture that encrypts your password before leaving your device. The only password you need to remember is your master password or the password of your password manager.
However, nothing is 100% safe online. If your device is infected by malware (a rare occurrence), hackers can hack your account. Moreover, enabling offline mode gives you offline access to your vault. You may risk giving someone access to your accounts once your device gets stolen or lost.
4. Delete inactive accounts
Inactive accounts, especially those linked to compromised old email accounts, may have weaker security and may be easy targets for hacking. Keep track of your accounts and delete inactive ones to reduce your vulnerability.
5. Set up two-factor authentication (2FA)
For added protection and security, you should also enable two-factor authentication on your iPhone. When turned on, you’ll be required to give two pieces of information, like a verification code and an SMS, to verify your identity before logging in to your account or doing specific actions, like changing important settings.
We also created a roundup of the best two-factor authentication apps for iPhone that you may want to consider.
Wrapping up…
Apple’s Security Recommendations is a handy built-in feature that alerts you if you have compromised accounts and informs you when your passwords are used somewhere else or may be too weak to secure your account.
Boost your security by reviewing the list and ensuring that your passwords are strong and unique. While it may be a hassle and time-consuming, keeping your data and accounts safe is worth it.
Read more:







Leave a Reply