Is your Mac excruciatingly slow? A virus could be one of the reasons behind it. The common misconception is that Mac is immune to viruses. However, the truth is that Mac is more likely to be infected by a virus/malware than Windows. Intimidated? Don’t be!
This article will walk you through common Mac viruses and how to remove them to protect your Mac.
- How to check if your Mac is infected with a virus or malware
- Types of known Mac viruses and malware
- How to remove viruses and malware from Mac
- Protect your Mac from viruses and malware
How to check if your Mac is infected with a virus or malware
It is important to find if your Mac is infected with a virus. Here are some telltale signs:
- The machine is noticeably slow
- A whirring fan
- Frequent crashes
- The malware could wreak havoc by changing your browser settings. If you are seeing intrusive unrelated popups, it could be the handiwork of malware.
You could save some time by investing in a good anti-virus program. However, anti-virus suites don’t come cheap, and not everyone can afford them. So before you invest in anti-virus software, let’s get you done with the basics.
Types of known Mac viruses and malware
The first step in getting rid of the virus is identifying which one is affecting your Mac. Thankfully, most of the Mac malware is already reported by others, making them a little easier to discover. Here, I will quickly walk you through the most common and potentially harmful Mac malware.
1. Adware.OperatorMac
Adware.OperatorMac has been around since 2015. It is persistent adware capable of reducing browser speeds. The adware automatically redirects traffic to ads. Furthermore, you might start seeing more ads on websites. In some cases, the attacker uses social engineering to redirect to malicious sites.
2. OSX.VSearch
OSX.VSearch is a macOS-specific malware. It turns text on the website into hyperlinks. The popups contain links to unrelated websites. Typically, the OSX.VSearch adware enters your system via bundlers. Software vendors use deception to bundle adware and install it without your permission.
3. OSX.Generic.Suspicious
OSX.Generic.Suspicious is a term associated with files that often get flagged as malware. The files are made up of suspicious content wrapped in the guise of a normal file. The OSX.Generic.Suspicious could unleash malware capable of controlling your Mac. Furthermore, the malware can damage your laptop and render it unusable.
4. Silver Sparrow
Silver Sparrow is a recently discovered malware. It has a dubious reputation as the first malware to target Apple’s new M1 chip. Silver Sparrow enters the system via Apple installer packages or .pkg files. The files include JavaScript code that runs even before the installation has started.
Users are deceived by a message that says, “This package will run a program to determine if the software can be installed.” In other words, even if you quit the installer, your machine will still be infected.
5. XcodeSpy
XcodeSpy is a relatively new malware that targets Apple developers. Typically, it spreads via malicious Xcode projects by using the run script feature in Xcode IDE. The malicious code housing Xcode spy can remain undetected. It is introduced via a third-party Xcode project.
The malware can record audio via mic, video via webcam, and keyboard input. That’s not all; XcodeSpy can also upload user files.
Further, if the malware infects your device, the attacker can access all your data, including banking credentials, private conversation, location details. In most cases, the attackers blackmail users for money or break into their bank accounts.
6. Adware.NewTab
Adware.NewTab disguises itself as a browser extension. It promises to track packages and flights. In reality, the malware pushes advertisements not originating from the site you are browsing. Moreover, the intrusive ads could slow down browsing on Mac.
7. Shyler Malware
Shlayer is an advanced type of adware that infects the system by tricking the user into believing it’s a Flash Player installer. Once installed, it uses a fake Siri message to warn about threats it found in macOS. Before that, Shlayer runs a malicious Mac Cleaner copy.
Hence, the user launches it to get rid of the viruses, and that’s when the real attack starts. It was first reported in 2018.
8. AkamaiHD.net virus
AkamaiHD.net is not exactly a virus or malware. Akamai runs one of the largest content delivery networks, and companies like Facebook utilize their services.
However, the majority of browser hijackers use Akamai for their hosting needs. This is the reason their URLs have the “akamaihd.net” extension. Further, browser hijackers can take control of the browser and access your browsing history. Typically, they hog computing resources and slow down your Mac.
9. Adware.IronCore
Adware.IronCore originates from an adware family published by IronSource. This particular adware targets macOS and is disguised in the form of a browser extension.
Further, security researchers have found out that Adware.IronCore is mostly installed by software bundlers. Attackers bundle popular programs with adware and offer them as a single installation package. As a result, unaware users often end up installing adware alongside the main software.
How to remove viruses and malware from Mac
We have listed the best and most efficient ways to get rid of the virus from your Mac. Some of these methods rely on system-level settings, while others require free-to-use malware scanning tools. With a combination of these methods, you can remove any Mac malware and virus.
1. Use Activity Monitor to kill suspicious processes
Infected programs often end up hogging computing resources. You can single out the virus by heading over to Activity Monitor and scouting for suspicious processes in this step. So, follow the steps below to identify and kill shady processes.
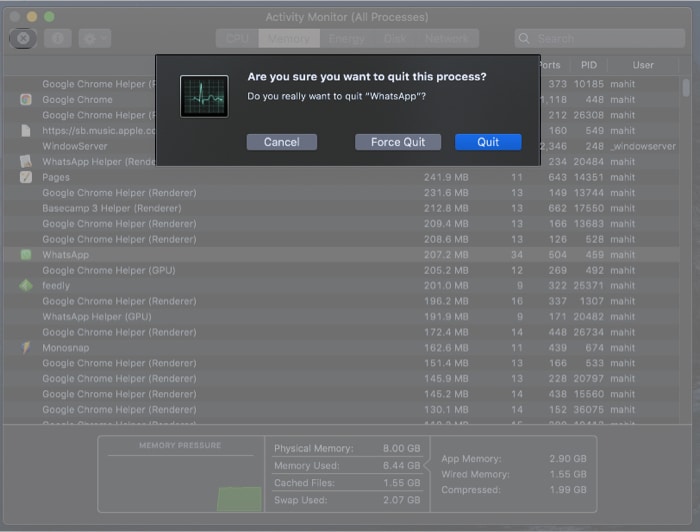
- Open Activity Monitor.
- Select the cross symbol on the left top corner, as shown in the above screenshot.
- When the system asks for confirmation, comply.
- Next, click Quit to kill the process thread.
2. Delete malicious programs
In the previous step, you have killed the process. However, the infected process will restart automatically. Thus, it is essential to delete the application.
Here’s how:
- Open Finder and select Applications.
- Search for any unknown applications.
Knowing malware names makes searching easier.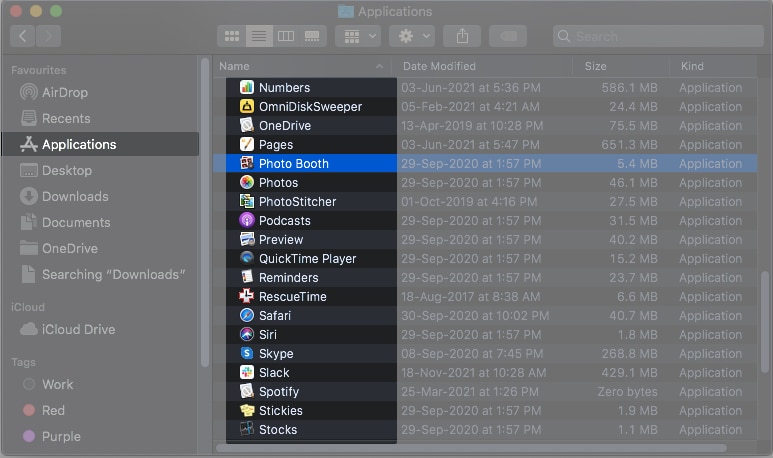
- Right-click the folder and choose Move to Trash.
Alternatively, you can drag the folder to the Trash - Empty Trash and restart Mac.
3. Browser housekeeping
With time, your browsing history and other elements like cookies and cache files will accumulate in temporary folders. Adware and other browser-based hijackers enter the system in the form of extensions. Further, they end up meddling with browser settings and redirecting to pesky ads. Follow the steps below to clean Chrome on Mac.
- Open Chrome.
- Click the More icon (three vertically stacked dots).
- Open Settings.
- Select Extensions.
- If you find an unknown extension, click Remove.
- Select Search Engine from the Settings menu.
- Click Manage Search Engines and remove any undesirable option.
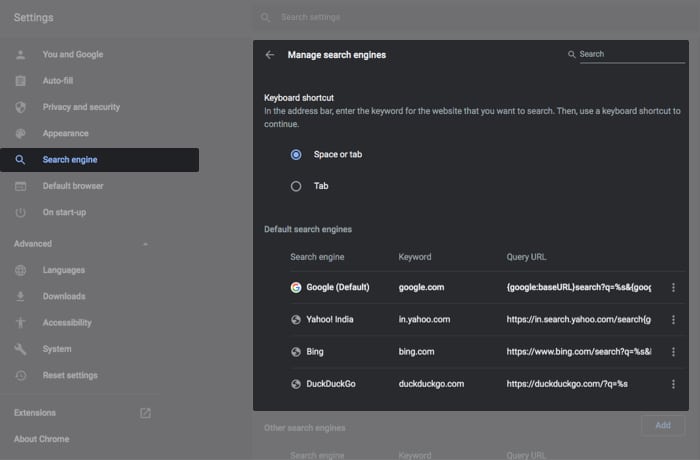
- Restart Chrome.
That’s it! You should be good to go.
4. Scan for malware
There is no dearth of malware scanning tools for Mac. However, most of them cost a bomb and do very little. I have been using the free version of Malwarebytes for quite some time, and it gets the job done. The tool not only scans for malware but also pushes the files to the Quarantine section.
- Download and install the free version of Malwarebytes.
- Open Malwarebytes → select Get Started.
- Choose Personal Computer → Use Malwarebytes free.
- Enter and verify the email address.
- Select Open Malwarebytes Free.
- Click Scan.
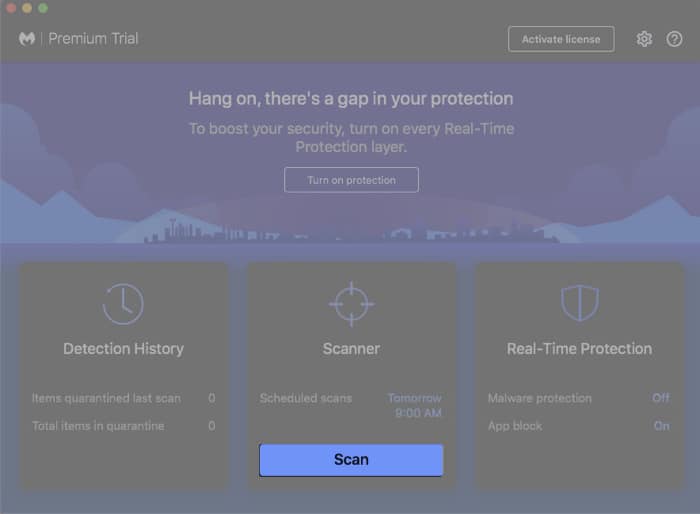
- Once completed, you will get to see a list of malware (if infected.)
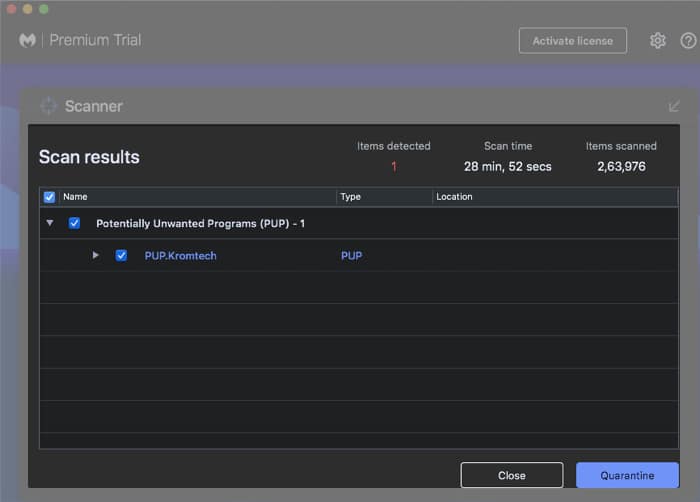
- Quarantine threats.
- Malwarebytes will automatically delete the infected files.
- Now, restart Mac.
How to protect your Mac from viruses and malware
macOS is designed to thwart a virus, malware, and other threats. The operating system comes with in-built security features. That said, it is always better to take precautions.
You can consider installing an anti-virus program. However, make sure you choose the right one. Some anti-virus programs don’t update their database. Thus, leaving your system exposed to the latest threats. Check out our explainer on how to protect Mac from viruses and malware.
Wrapping it up
Attackers are getting crafty when luring users to install or download malware. Over the years, social engineering techniques have evolved and are now harder to detect.
We hope this article has helped you identify and reclaim your Mac from the malware. Do you use anti-virus for Mac? If yes, which one? Share in the comments below.


Thanks for a great and very useful article!
For the activity monitor, you’re missing the screenshot. What is the cross symbol you’re referring to? Is it under CPU, memory or? And how do you even know what is suspicions activity to sélect?
The cross symbol I referred to is not a literal symbol in the Activity Monitor. It was meant to convey that you should look for any suspicious or unnecessary processes and terminate them. In the Activity Monitor, you can find it by selecting the process and clicking the “X” button (Quit Process) at the top-left corner of the window.